How to build a system with secure flash storage?
In modern automotive embedded systems, highly secure data storage is essential, especially when facing increasingly sophisticated cyber attacks. The need for electronic embedded systems for safety and security has never been stronger. As cars become more automated, we need to increase their level of security to prevent them from being compromised by hackers. The same is true for factories with a large number of robots and Internet of Things (IoT) devices that need to process sensitive data.
For all such embedded systems, non-volatile flash memory is essential. Flash memory can be used as code storage, file system storage, or microcontroller unit (MCU) memory to run code directly. To achieve system security, you must first ensure that the flash memory used by the system is secure. This article explores the security needs of flash memory to help developers build secure and secure embedded systems for automotive, industrial and communications applications.
If we look closely at the electronic systems of modern cars, we will find that flash memory is widely used throughout the car. As the complexity of the system increases, we need larger capacities for code storage and data storage. All subsystems in the car, including advanced driver assistance systems (ADAS), instrumentation systems (coming soon to be merged with infotainment), transmission and body systems, require embedded systems to run in real time. All of these embedded systems require some type of flash memory for code storage and data storage. Figure 1 shows an ADAS subsystem using multiple NOR flash devices.
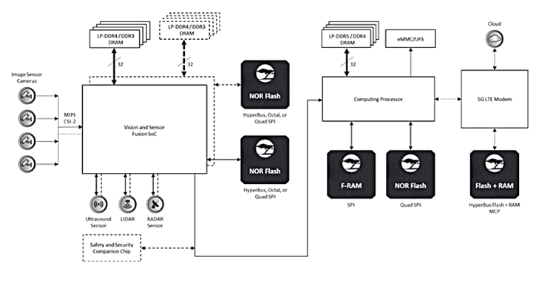
In today's ADAS applications, complex algorithms and artificial intelligence processes rely on code and data stored in flash memory to run. Storage must provide fail-safe and safety protection, as system failures or malicious attacks can cause serious personal injury or even death.
Similar safety and security requirements for storage solutions exist in industrial and network applications. In the context of increasing connectivity, hackers can break through any weak entity connected to the Internet, steal sensitive information, or use the compromised device as a springboard to launch attacks elsewhere in the network. Therefore, it is important to build a security system to avoid this type of attack.
Flash memory vendors have provided pure data storage for years. For these applications, endurance and retention are the two main indicators of flash memory quality. Security is not a requirement for this type of flash memory device, which means that the data stored on the flash memory is either completely unprotected or protected with uncertified commands.
For example, some flash memory devices provide basic protection functions through the normal command set, such as non-volatile or volatile protection of sectors for program or erase operations, password protection for program or read operations, and so on. Although these functions are good, they are not enough to defend against sophisticated attacks. If hackers have access to the bus interface of the flash device, they can easily extract or modify data on the device. To ensure security, flash memory devices must protect stored code and data from multiple means. The following summarizes several attacks that flash storage devices need to protect against.
To prevent the system from being permanently damaged if the key is compromised, a temporary key is usually required. The temporary key expires after a certain time or after a certain number of times. The purpose of this is to prevent the key from being decrypted by destructive physical analysis (DPA) or other iterative attacks. Another man-in-the-middle attack is to replay intercepted legitimate messages after a certain time. To prevent replay attacks, the host and the flash device must generate a MAC using an accumulation counter. Because the current accumulation counter value is different from the value of the previous message. Replaying the same message will not pass MAC verification. Some hackers can use advanced technology to read the entire contents of the flash memory chip and make profits through illegal cloning. To prevent such attacks, each flash chip must have a unique device secret (UDS) that no one can read. The UDS value is unique and is a true random value within each chip. There is no correlation between UDS in one chip and another.
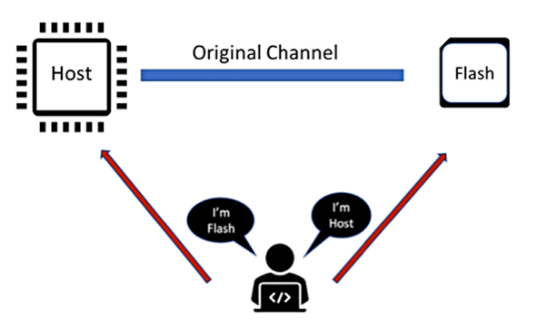
Hackers in MIM attacks often imitate the sender of the communication channel and send commands or messages to the other side to steal or modify data. Therefore, it is necessary to authenticate every message between the host and the flash device. Authentication can be achieved by using public keys on the host and flash memory to generate a message authentication code (MAC) that accompanies the actual message. The receiver can verify the MAC before taking action on the message.
UDS can be used to derive the Composite Device Identifier (CDI), which is the basis for generating Device ID Certificates as defined by the Trusted Computing Work Group (TCG) Device Identifier Combination Engine (DICE) specification. Generally speaking, the device also generates an alias private key public key pair for all the keys derived from the host on the basis of CDI. This eliminates the need to expose the private key of the device ID. With UDS and DICE processes, hackers cannot clone devices because UDS is not physically cloneable.
Passive listening is another known attack. By eavesdropping on the bus, an attacker can collect sensitive or confidential information from the data transmitted through the bus. To protect important data, users can choose to encrypt the data before sending it to the flash device via the bus and storing the data. When the host retrieves data from the device, the data should also be encrypted, so that potential hackers can never be exploited. Some people may say that the encryption method does not require a secure flash storage solution because the host can directly encrypt the data and store it in flash memory. Only the host can decrypt the data.
However, there are certain disadvantages to doing so. One of them is that the host cannot easily discard the encryption key. For example, suppose KeyA is used to encrypt data and store it in flash memory. Later, users find that KeyA has been breached, and they need to use a different key on the system, namely KeyB.
At this time, the host is in a dilemma: it cannot directly discard KeyA, because it needs to retain the key in order to decrypt the data read from the device. However, if KeyA is breached, users may not want to keep it permanently. If you want to use the new data encryption key, users have to take more complicated measures. Erase the original encrypted data on the flash memory before programming the flash memory with the newly encrypted data. This kind of operation is not easy at the scene and there are certain risks.
On the other hand, if the secure flash memory can provide encryption and decryption functions, it can safely store the plain text data in its secure storage and encrypt it before sending the data back to the host. If the current encryption key is compromised, the host can simply exchange a new key with the device. Keeping data intact and secure is a much simpler approach than storing encrypted data.
If you want to know more, our website has product specifications for the flash storage, you can go to ALLICDATA ELECTRONICS LIMITED to get more information

